Sonicwall is one of the leaders in the cybersecurity and next-generation firewalls market. Also, this is one of the first companies that recognized a need for networked cybersecurity and observability on-prem and in the cloud. Their products can be physical, aimed at a wide range of customers from SMBs to Large enterprises, as well as virtual firewalls. Today we will configure virtual NsV 270 for NetVizura products.
NetFlow configuration
SonicWall next-generation firewalls (NGFW) are, if not the best, then one of the best environments for configuration. They offer an almost unparalleled number of options for any configuration. So, as said, our focus is on SonicWall NSv 270 here. In the case of NetFlow, we go to Device on the ribbon bar and opt for Device/Appflow/Flow reporting. Then, reenact the example below (note: port 2055 is usually the default port for the NetFlow):
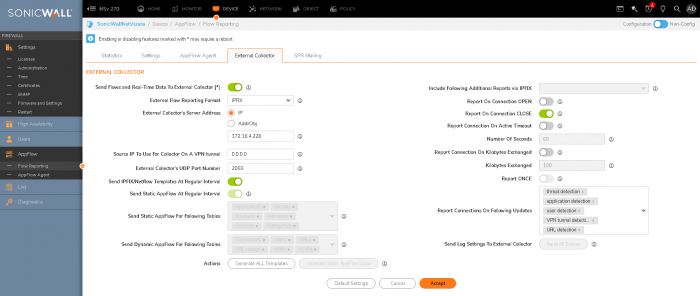
Afterward, check your firewall rules, and if everything is allowed, the traffic should start flowing. To enable SNMP, visit Device/Settings/SNMP and configure similarly to our example (remember: don't leave your community name to public):
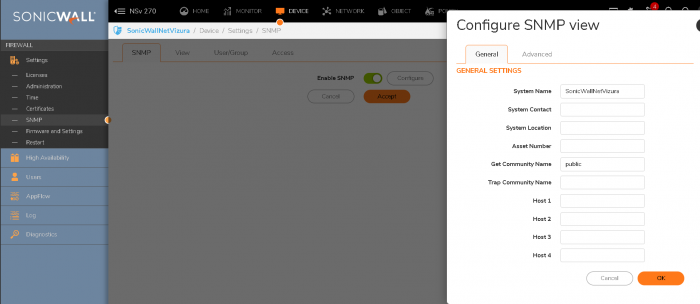
Upon completing the configurations we have displayed, you should see traffic in NetVizura Netflow module, with resolved names.
EventLog configuration
When we come to the Syslog configuration, there is a limited list of options for the regular EventLog collector. Go to Device/Log/Syslog, and again follow our illustration (note: port 33514 is usually the default port for the Eventlog module):
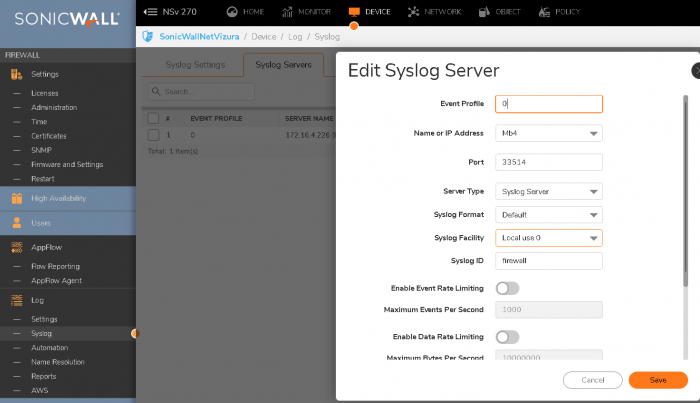
Now, Syslog messages should also be flowing to the NetVizura EventLog module.





