Palo Alto Networks is one of the most famous cybersecurity companies, mainly known for their next generation firewall devices. Their Operating System, PAN-OS is renowned for its ease of use and numerous configuration options. One can configure everything around router only by using GUI, which makes it perfect for small companies and SMBs that don't have dedicated Network Engineer.
NetFlow Configuration
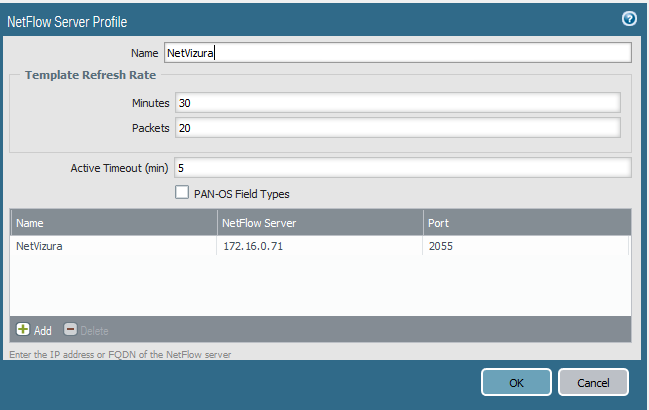
First we need to create NetFlow server profile via Device/Server Profiles/Netflow. There one can configure usual parameters (NetFlow name and Server/Port), as well as template refresh rate (in packets and minutes). The firewall refreshes the template if either one of the aforementioned thresholds is overdone. Active Timeout is frequency in minutes at which firewall exports NetFlow records (default is 5). Example is shown in an image below:
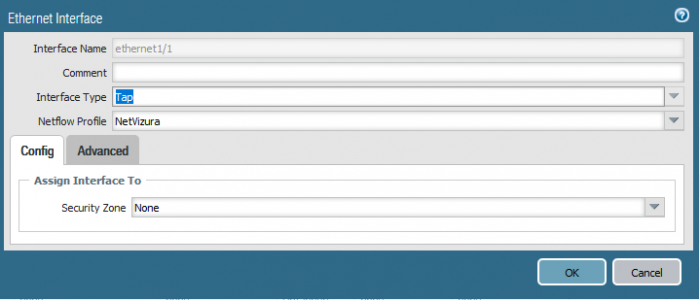
Now apply server profile to the interfaces from which NetFlow data should be exported. Go to Network/Interfaces/Ethernet, edit interface data and select the profile we have just created.
Once you have gone through the simple settings mentioned before, NetFlow traffic should appear in your NetFlow collector.
EventLog Configuration
To configure EventLog export, we need to go through a few steps before having messages in our Eventlog Analyzer.
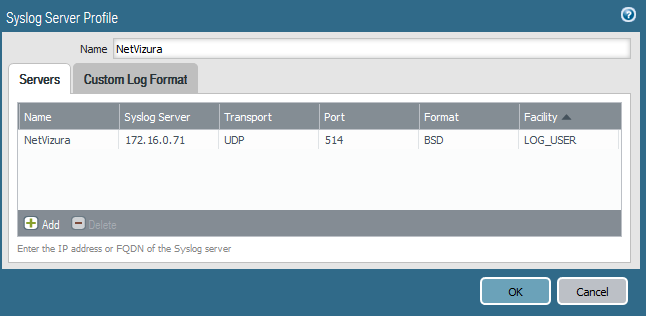
Start by creating Syslog server profile, possible on the following location: Device/Server profiles/Syslog. Usual configuration can be seen in the screenshot below:
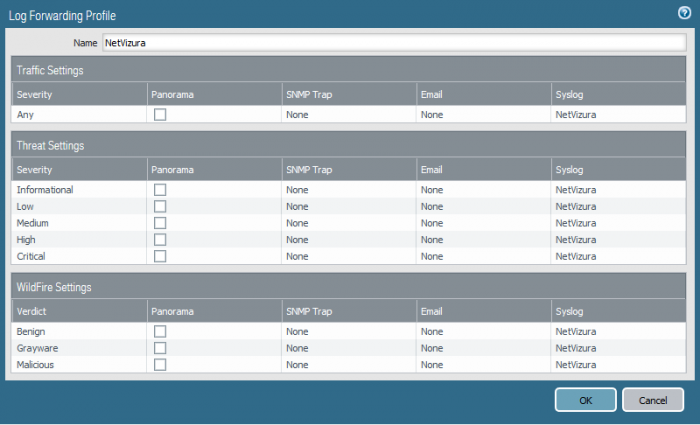
Afterwards, configure Syslog forwarding for your traffic. Go to Objects/ Log Forwarding in order to configure Log Forwarding Profile, in a similar way as we did in our example below:
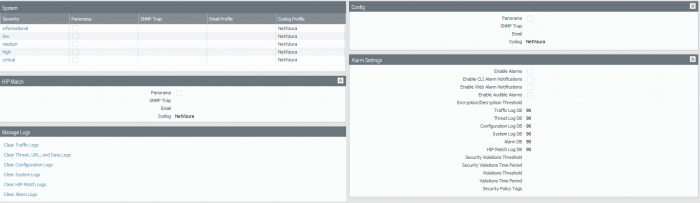
Hereafter, Syslog forwarding for System, Config, HIP Match and Correlation logs should be configured in Device/Log Settings. The recommendation is to configure forwarding for System, HIP Match and Config logging.
Finally, click on the Commit button and messages should start flowing to your EventLog Analyzer. As simple as that!
Syslog configuration in Palo Alto devices is incredibly smooth. There are numerous optional steps, from configuring header format of the syslog messages to securing syslog communication (if needed). However, few settings mentioned in our text are enough to catch each and every message and set monitoring and alerting on them.





